Remote Access To IoT Devices: Your Guide To Secure SSH
Can you truly harness the power of your Internet of Things (IoT) devices from anywhere, at any time? The answer lies in the strategic implementation of remote access platforms, transforming your control over these devices from a logistical challenge into a seamless, accessible reality.
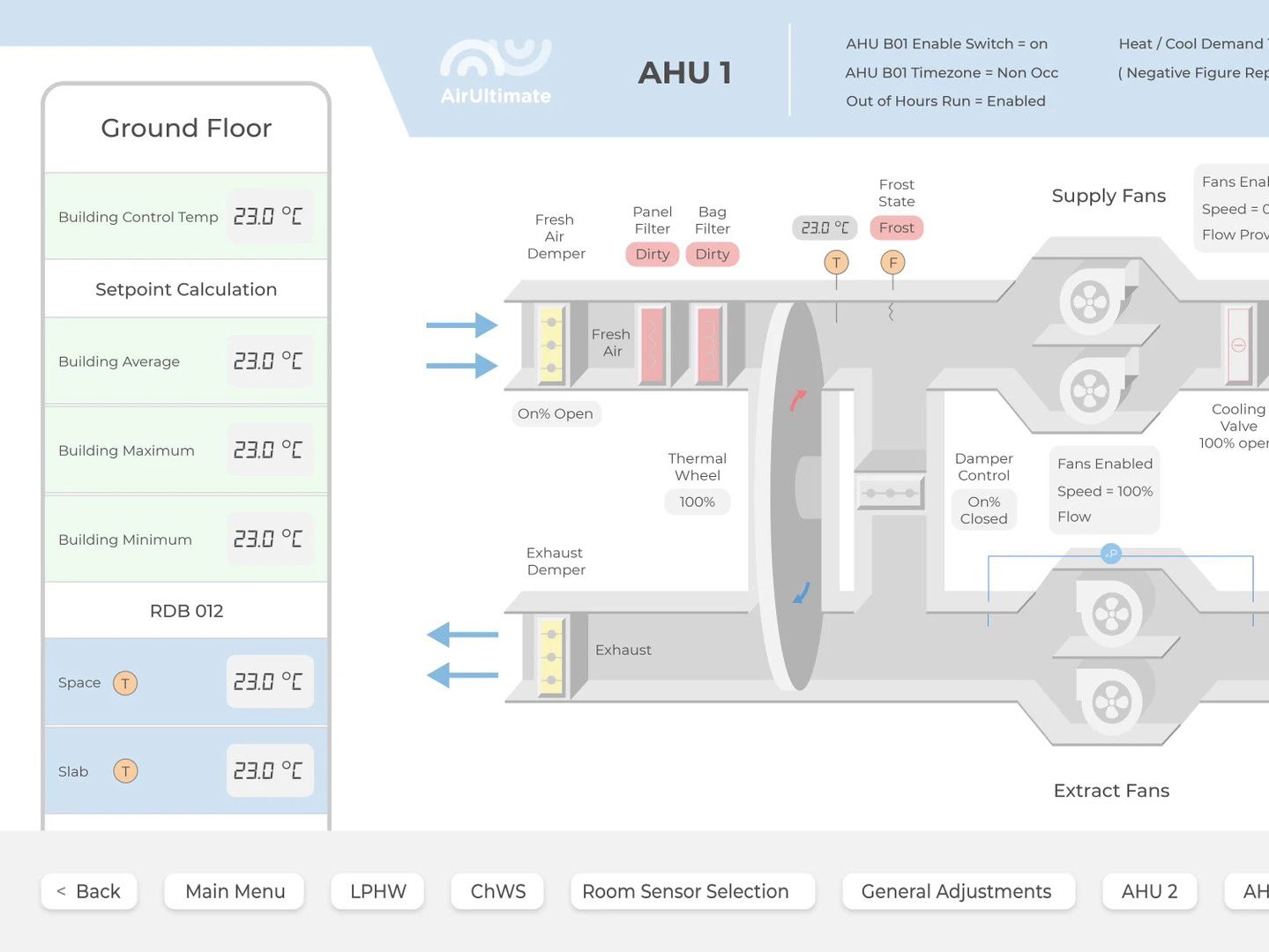
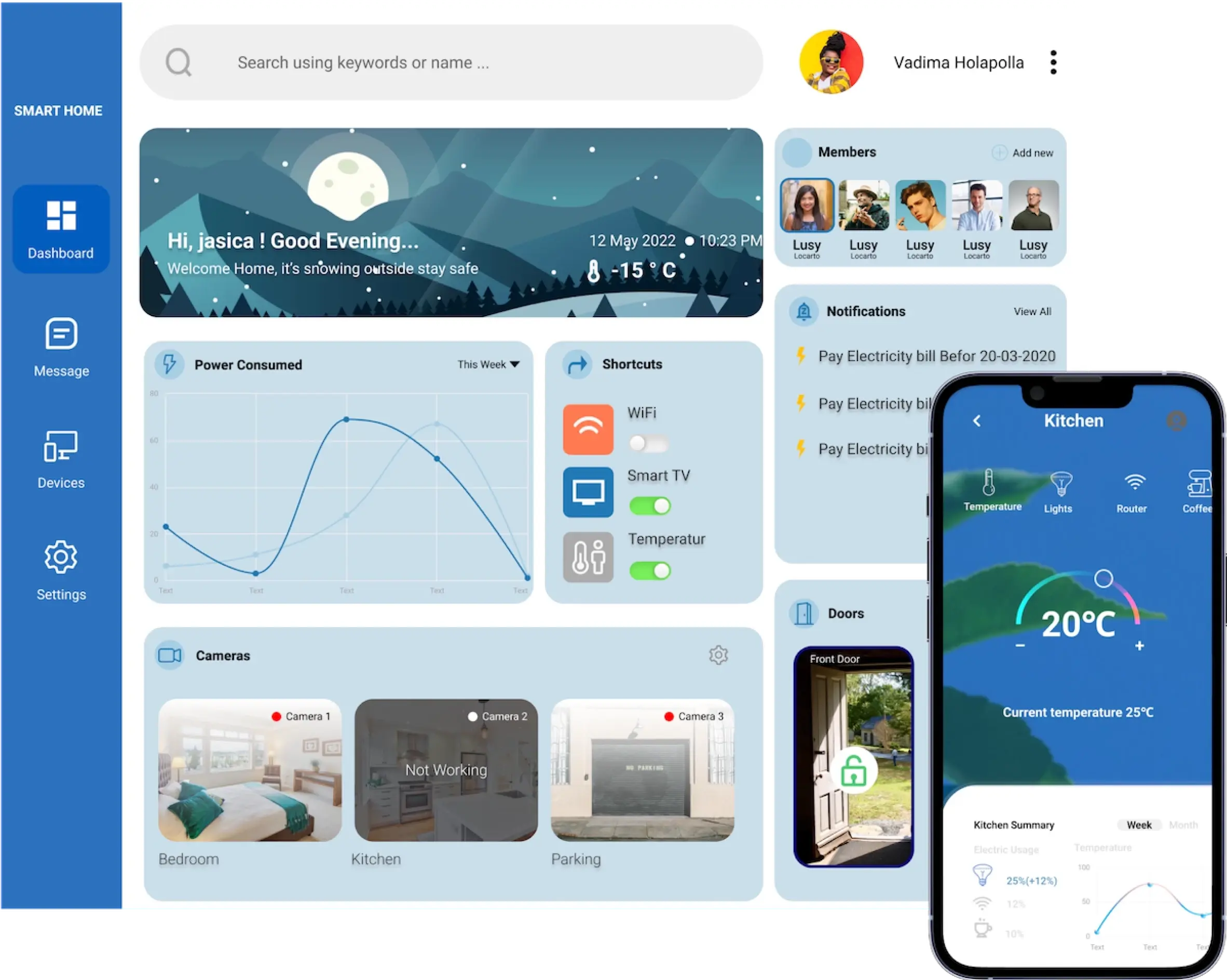
In an era defined by interconnected devices, the ability to remotely access and manage your IoT infrastructure isn't just a convenience; it's a necessity. From smart homes and industrial sensors to complex raspberry pi fleets, the need to control these devices from afar is paramount. This capability allows for real-time monitoring, proactive maintenance, and the ability to respond quickly to any issues that may arise. The rise of cloud-based IoT device management platforms, like SocketXP, exemplifies this trend, offering comprehensive solutions for managing and monitoring these devices, setting cloud alerts, and executing batch jobs.
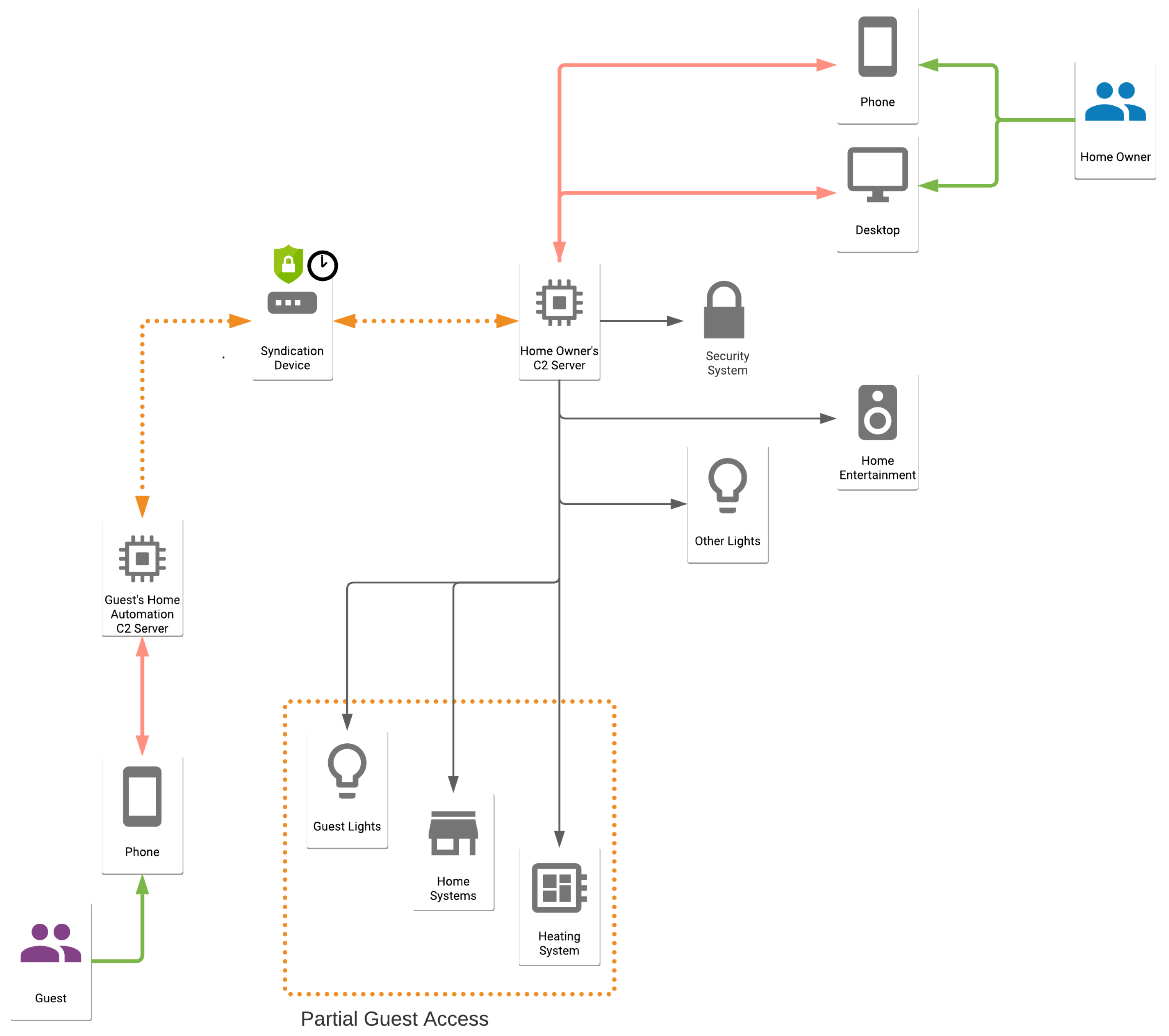
A cornerstone of secure remote access is the Secure Shell (SSH) protocol. SSH provides an encrypted communication channel, ensuring that all data transmitted between your device and the control center remains protected. This is critical in preventing unauthorized access and maintaining the integrity of your IoT ecosystem. The integration of SSH key management, as seen in platforms like SocketXP, further enhances security. These platforms offer a single pane of glass for managing all your SSH keys, quickly identifying key owners, associated systems, and access levels. This streamlines the process of managing user access and reduces the risk of vulnerabilities.
Let's dive into the core of the matter. Remote access is the key that unlocks the full potential of your IoT devices. Platforms like remoteiot empower users to control their devices via a web browser, offering unparalleled convenience and accessibility. Similarly, the ability to remotely manage a raspberry pi fleet or any linux machine, regardless of its location behind a NAT router or firewall, is a game-changer. Solutions like SocketXP make this possible.
The setup of SSH public/private key pairs adds another layer of security. Using your own SSH clients, such as PuTTY, allows for more secure remote access to your IoT devices. This approach ensures that only authorized users can establish a connection. Furthermore, by establishing an SSH tunnel, you can securely access devices within a private network through a series of encrypted connections. It's like creating a secure pathway within a larger, secure pathway.
The evolution of IoT device management platforms is continuous. These platforms are evolving to provide better security features. This commitment to continuous improvement shows the dynamic nature of technology. In order to maintain the security and efficiency of your IoT devices, it is critical to implement these security features.
Here's a comparative look at various platforms, focusing on their SSH key management capabilities:
| Platform | Key Features | SSH Key Management | Raspberry Pi Focus | Pros | Cons |
|---|---|---|---|---|---|
| SocketXP | Cloud-based, remote access, device management, cloud alerts, batch jobs. | Comprehensive suite, single pane of glass, key owner/system/access level visibility. | Yes | Easy to use, simplifies key management, secure access via SSH. | (To be filled based on specific platform limitations/costs if known). |
| Tailscale (for comparison) | Secure networking, zero-config VPN, access control. | Simplified, no manual SSH key config. | Yes | Simplified setup, easy SSH access. | Reliance on Tailscale infrastructure, potential learning curve. |
| Remoteiot (Example) | Remote control via web browser, VNC integration. | (Specific details would need to be determined based on the platform.) | Yes, VNC support. | (To be filled based on platform features) | (To be filled based on platform limitations/costs if known) |
| Generic SSH Server with manual setup | Basic SSH access. | Manual key management, potentially complex configuration. | Yes | Flexible, open-source. | Requires technical expertise, prone to errors, more manual work. |
For detailed and current information, please refer to the official documentation of each platform. Here's a link to a well-regarded resource on SSH key management and IoT: SocketXP's official website.
One of the key components of secure IoT management is using SSH keys. By establishing secure access to your IoT management platform with SSH keys, you can ensure that only authorized users can access and control your devices.
The core function of an IoT management platform via SSH is to secure and manage devices using SSH protocols. SSH provides encrypted channels for secure communication. This is a fundamental part of current technological infrastructure and provides a secure connection.
Choosing the right remote IoT platform is crucial. The market offers a diverse range of options, each designed to meet specific needs and preferences. Some platforms are more user-friendly, while others offer a greater depth of features. Understanding the characteristics of the different platforms is crucial for making a choice that suits your particular circumstances.
For those who want to remotely control devices, the remote iot platform offers a solution. This platform allows users to control devices via web browsers. For users who are familiar with the raspberry pi, there is the option to set up a VNC server. Using a VNC client application on any device allows you to monitor and communicate with your device. The user can connect the raspberry pi and the VNC client from any location with an internet connection.
The world of IoT management is consistently evolving. As technology progresses, these platforms adapt, providing more features. With innovations like immediate key cleanup, these platforms can guarantee security. The development of remote management IoT platforms illustrates the continuous improvement of technology. It is necessary to implement new features, and updates to maintain security and efficiency.
The goal of any well-designed IoT platform is to enhance accessibility. By providing convenient access to your devices, the platforms promote an environment for innovation and enable users to quickly respond to changing conditions. The platforms offer the tools needed to take full advantage of the capabilities of linked devices, from setting up easy access to real-time surveillance and automated job execution.
The use of SSH keys as a cornerstone of security cannot be overemphasized. These keys provide a solid framework for access control, protecting your IoT devices from unauthorized access. The implementation of SSH keys is more than a technical setting; it's an act of due diligence for ensuring the safety and integrity of your devices.
In terms of managing your raspberry pi devices, platforms are designed for managing SSH keys. It is important to check the features of a platform prior to selecting it. This would help decide how much work you need to do to set up your system. For instance, easy setup can be provided with platforms like tailscale, which eliminate the necessity to set up SSH keys manually. Other platforms provide detailed key management features. Each option has different capabilities.
In order to provide more secure SSH access, public/private key pairs can be employed. The utilization of own SSH clients such as putty improves the process. After the initial step, another SSH connection can be set up via the SSH tunnel by the client machine. This creates a more safe connection for handling devices.
The remote access to IoT devices is a cornerstone of contemporary technological advancement. It gives users the ability to observe, manage, and engage with their linked devices from any place in the world. This control helps with the effectiveness of operations, and the capacity to rapidly respond to incidents.
In today's world, where devices are interconnected, IoT device management platforms are constantly evolving. They incorporate remote SSH as a core feature. The design of these platforms addresses the changing safety demands of our interconnected environment by delivering a reliable and safe way to interact with and control IoT devices.